Most developers use IDEs for their daily work. They use them to write code and compile it to make different applications. IDEs provide a complete environment to run and execute programs written in a particular language so it’s convenient for them.
Writing code, building applications, and executing them is one part of the software development lifecycle. There’s another important part of this too which is the identification of security issues and loopholes in your code.
For this, a variety of tools provide IDE integration that you can integrate into your development environment and then use them to figure out issues in your code.
Let’s look at some of the open-source options out there.
1. SonarQube
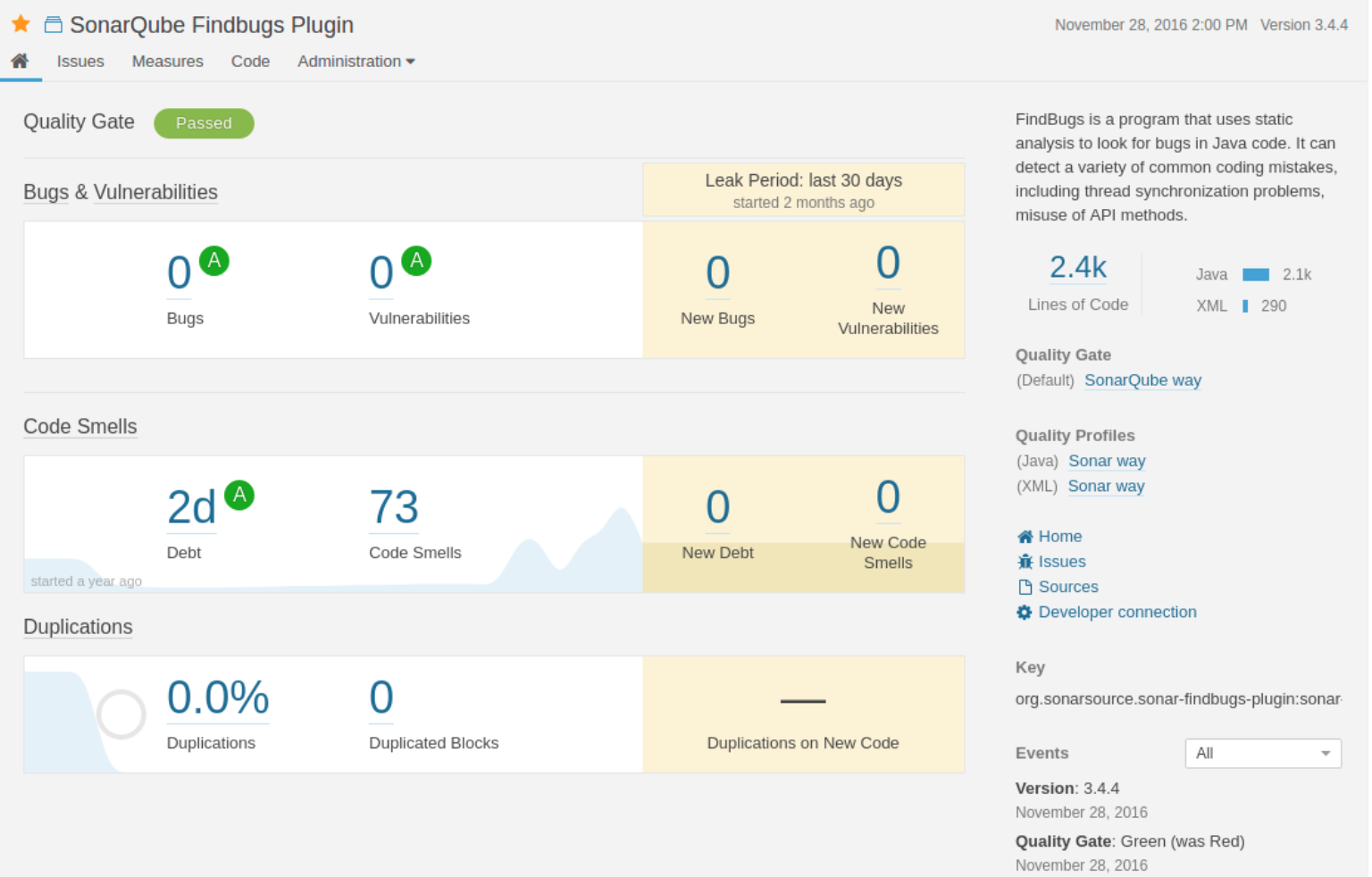
SonarQube Findbugs Plugin
SonarQube is a tool that supports around 20 programming languages and offers a static analysis of your code by giving you the power to detect vulnerabilities related to security, bugs, and other related issues.
It actually does an analysis of your code and then provides a detailed report you can view. It sees the code from different aspects and hence ensures there’s no weaknesses or vulnerabilities moving from module to module.
It’s primarily written in Java but it has plugins alongside web tools that extend its functionality. Moreover, it gives you several customization options.
2. WhiteSource
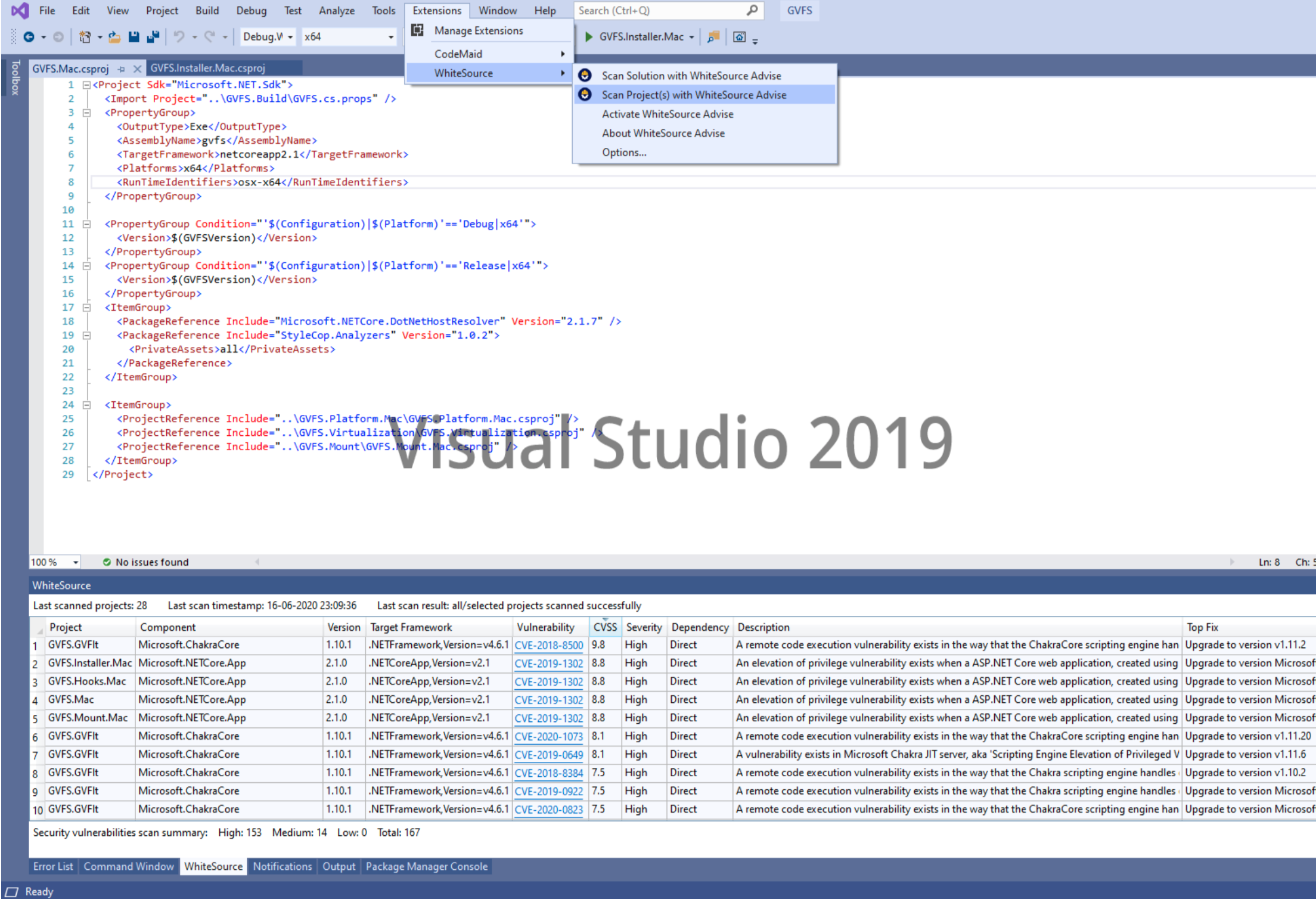
WhiteSource IDE Integration with Visual Studio 2019
WhiteSource is a security compliance platform for your open-source codebase. It provides out-of-the-box integrations for all of the major IDEs like IntelliJ, Visual Studio, Eclipse IDE, and Visual Studio Code.
Whenever you add an open-source package or module to your project, it will be analyzed by the WhiteSource plugin or extension. If some vulnerabilities are found in it, WhiteSource will highlight those issues for you and also let you know the ways to fix those problems.
Another good thing about WhiteSource is that you can integrate it into your workflow as well as GitHub, BitBucket, or GitLab repositories so it can do all the static code analysis and vulnerability detection on-the-go.
WhiteSource has a free trial version. After that they have different pricing plans you can choose from.
3. FOSSA
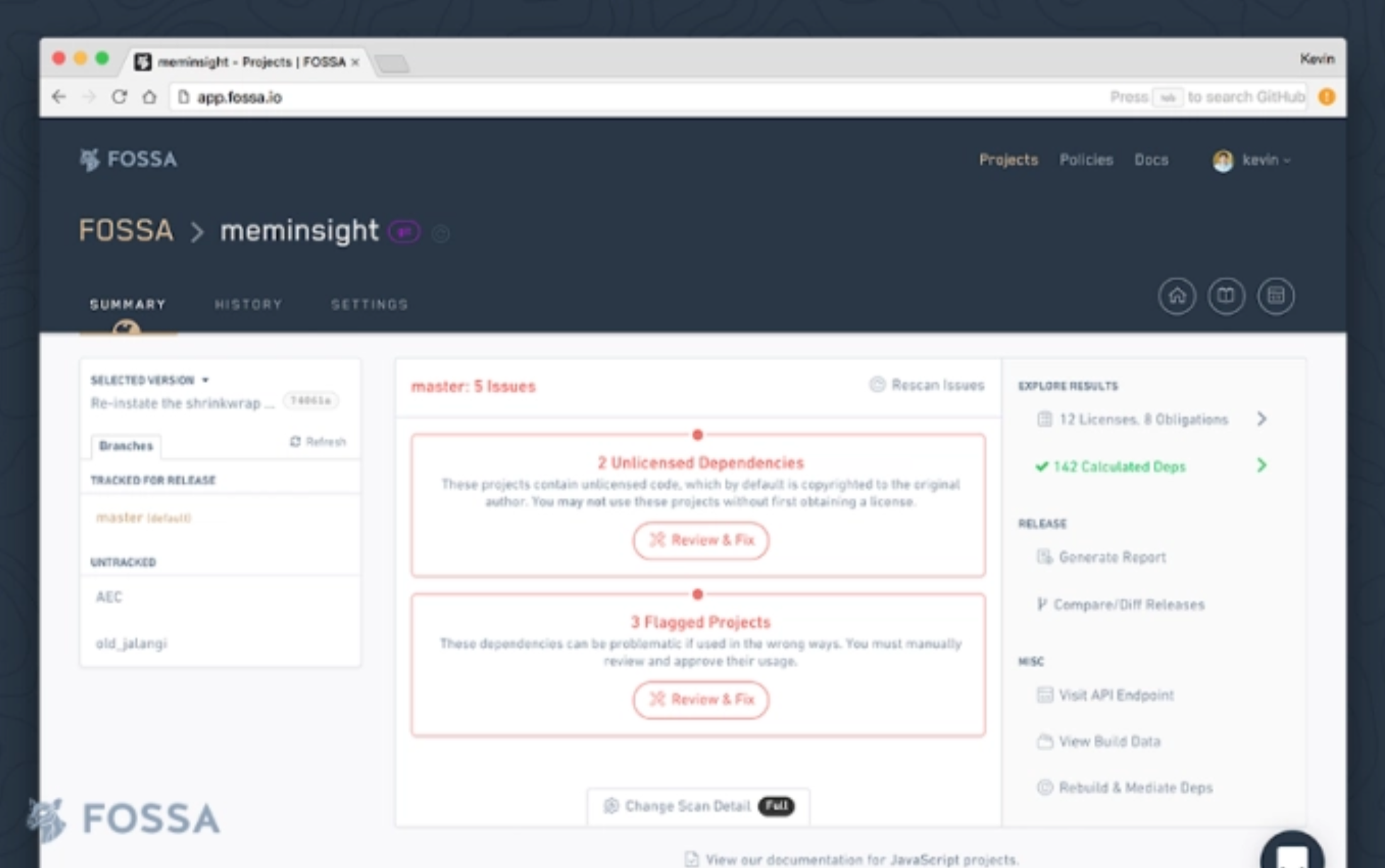
Fossa tool UI
FOSSA is another tool for dependency analysis for any of your codebase. It supports both vulnerability and license scanning for large monolithic codebases.
The main advantage of FOSSA is that it’s language agnostic and supports more than 20 languages and runtime environments. Also, it’s cross-platform and has a command-line CLI as well. Providing built-in integrations with all of the major IDEs it’s another great tool to use.
FOSSA is completely open-source and you are free to use it for both commercial or personal purposes in your hobby projects
4. RetireJS
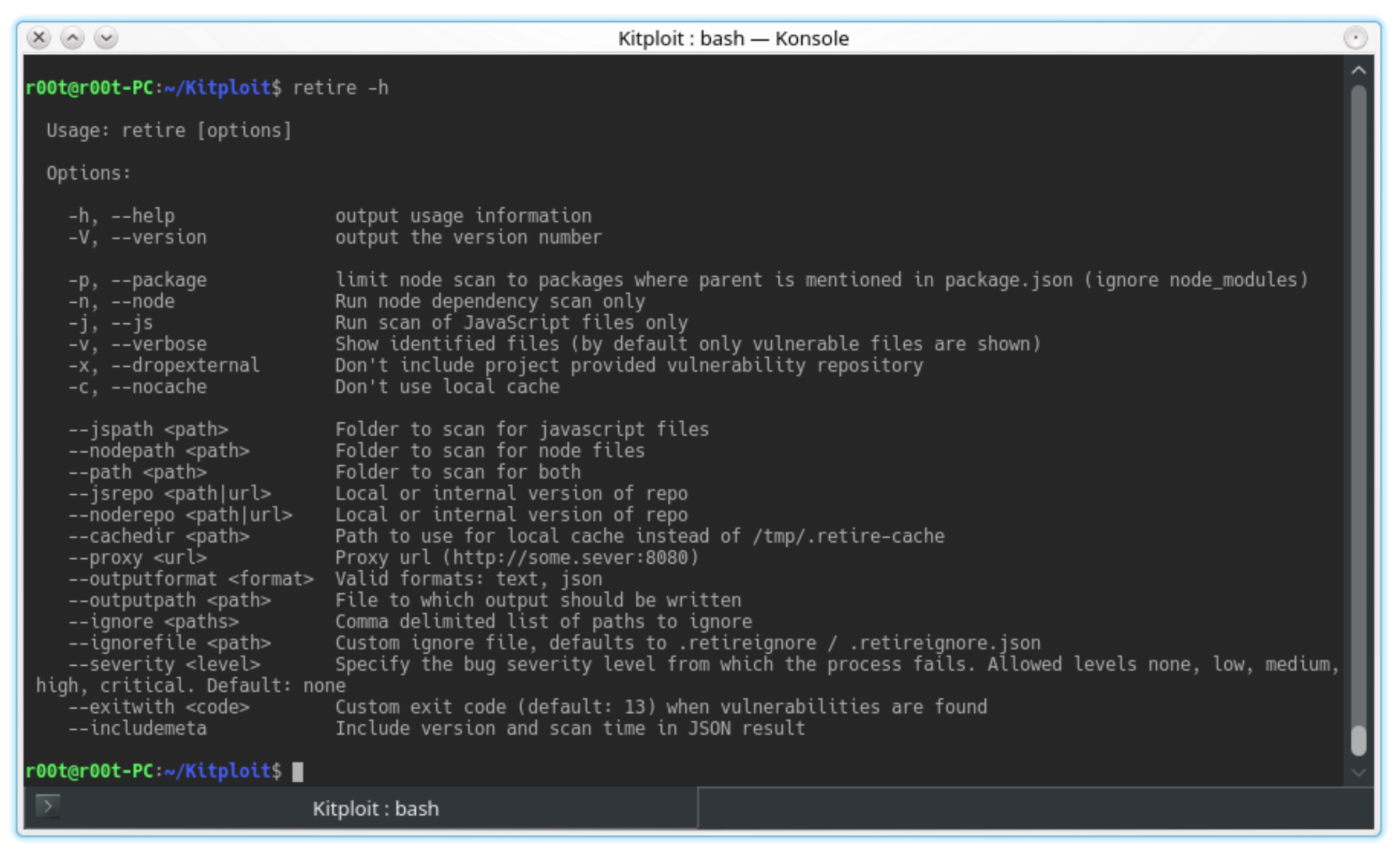
RetireJS CLI
RetireJS is an extension and plugin for scanning web applications for vulnerable Javascript libraries.
A big advantage of RetireJS is that it’s available in many forms like command line scanner, grunt plugin, gulp task, chrome, and firefox extension and as a burp suite and Zap plugin.
You can load the web application to be tested in your browser. After that, RetireJS will scan it for any vulnerable plugins, packages, or libraries. In the address bar, there will be an icon displaying if any vulnerable package was detected or not.
The main problem in the JavaScript Ecosystem is that you have a plethora of packages, libraries, and tools. You never know which package may have some unknown vulnerability. Also, some are not actively maintained so they may have some issues due to insecure code. RetireJS solves this exact problem for you and frees you from having to check version numbers and vulnerabilities in every package manually.
Conclusion
Security is a really important aspect of software development that is often neglected. Usually, the main focus is on performance, scalability, and code structure but it’s not only important to make a scalable application, security matters a lot too. A vulnerable application can sometimes even cost more than the price of that software system.
When working in teams, often such things are neglected. So, it’s always a best practice to integrate these tools into your software development pipeline so that no one misses this and leaves something vulnerable in the codebase.
