
How To Deal With Common Open Source Vulnerabilities
Most successfully IT Companies like Google, Microsoft including small Saas organizations relies on open-source software to power their software and applications architecture, deployments and so on. It really helps speed up the rate at which developers work on a project and also gives developers access to a myriad of top-notch projects.
Open Source has a lot of features and advantages for both organizations and developers since they can take advantage of a variety of open source projects that would be time-consuming to build. However, even with these advantages, it comes with its own drawbacks and a fair amount of exposure to different kinds of vulnerabilities which pose a significant risk.
The open-source system works on a voluntarily and collaborative basis, which means that a group of different developers voluntarily maintains and updates each open source project. These open-source projects rarely go through a similar level of security checks as compared to commercial software which may lead to unnoticed vulnerabilities. Few of the developers working on these projects have advanced security knowledge and vulnerabilities may go unnoticed even with a large developer community reviewing the code.
A huge number of applications can become exposed to a vulnerability found in a single open-source dependency as it can give a level of access to hackers. Open-source dependencies is another security risk. Without an accurate inventory of open source dependencies for different applications, vulnerabilities can slip under the radar.
In this article, we’ll explore ways to deal with common vulnerabilities in open source code.
Set Strict Security Rules and Standards
The first step to deal with open source vulnerabilities is setting strict security rules and standards on open source dependencies developers use. Ensure each open-source dependency used does not have any known vulnerabilities. Require that developers check open-source components for either disclosed or undisclosed vulnerabilities before using them.
Most developers are currently still unaware of the risks posed by different open source components and dependencies. It is very crucial to help them understand that vulnerabilities brought from open source components into the application can put the whole app at risk, if not the organization as a whole.
The simplest way to employ this is to create and enforce policies that either require the security team to approve of open source components or require developers to prove the security of the tool. With this in place, you automatically improve the security of your application by making developers aware of such risks.
Monitor the Open Source Components/Dependencies Used by your application
Monitoring the open-source components/dependencies your application is using constantly really helps discover any known or unknown vulnerabilities that exist in them. Most open-source projects can contain both known vulnerabilities and unknown vulnerabilities.
Publishing a vulnerability can help in tracing the possible security flaws that already exist in an application’s dependencies. So its always a good idea to report a vulnerability when one is discovered while monitoring.
This makes it easier for people to identify, find a fix, test it against the reported vulnerability and apply the fix for future updates.
In order to deal with open source vulnerabilities, enterprises, developers, and individuals need to start keeping track of their application dependencies and their vulnerabilities.
Keep track of security updates for dependencies
While monitoring your application components or dependencies, you need to also keep track of their security updates.
You need to have an updated inventory of your organization’s open-source libraries, both in development as well as in production because it goes a long way in securing your open source components. A lot of developers, organizations don’t really know the full details about the open-source components and their child dependencies they are using currently in their applications. This serves as a major security threat everyone needs to know about.
Most popular proprietary applications have indirect open source components with child dependencies that might not be in active development or has an outdated version. These open-source components remain unpatched and become insecure over time.
Most developers spend their resources and time on securing and improving the in-house components. Thereby, ignoring the security updates of the OSS components their applications are using opens up loopholes that will go unnoticed.
A good head starts in fixing this is by making developers track what open source components they use and the last time these were updated. This makes it easier to know how updated the developers are with open source component security, as well as a list of dependencies in use.
Test Your Open Source Components and Dependencies
The best way to ensure and improve the security of your open source components is to test the security of open source components being used within your organization once they’ve been identified.
Analyzing the Open Source component is very important because the code could hold unknown security vulnerabilities, and also its dependencies and functions may differ between different use cases. In cases like this, only testing and code review can identify these issues.
Ensure you build gate checks, constraints, and validations for your components and dependencies so that some of the milder vulnerabilities in your dependencies won’t have an impact on your whole application.
Employ The Use Of Open Source Security Tools
A huge number of different open source and commercial tools and services have been developed over the years to deal with the issue of identifying security vulnerabilities in open source components. Each security tool or service has its own specialty and deals with each problem a little differently.
However, the end-result matter since they are in place to deal with vulnerabilities in open source projects.
Below are some of the best tools to use:
WhiteSource Bolt: This a commercial tool that currently supports Ruby, NPM, PHP, Python, and Bower. It has different tools that can be used to tackle any kinds of open source vulnerability issues.
NPM Audit (previous NSP): The NSP is known largely for its work on Node.js modules and NPM dependencies. The latest version of NPM integrates NSP to implement the NPM audit script. It checks for any known vulnerabilities in your node modules and related dependencies and offers support for patching those vulnerabilities.
RetireJS: RetireJS is a popular open-source dependency checker specific to JavaScript. Its unique selling proposition (USP) is its ease of use. RetireJS contains multiple components, including a command-line scanner, as well as plugins for Chrome, Firefox, Grunt, Gulp, ZAP, and Burp.
OSSIndex: OSSIndex is a tool that supports several different technologies. It effectively covers JavaScript, .NET/C#, and Java ecosystems. It also provides API vulnerability for free.
Dependency-check: Dependency-check supports Java, .NET, and JavaScript, as well as Ruby. It pulls its vulnerability information from the NIST NVD.
GitHub Security: GitHub provides the infrastructure security researchers and open source maintainers need to report and disclose security vulnerabilities.
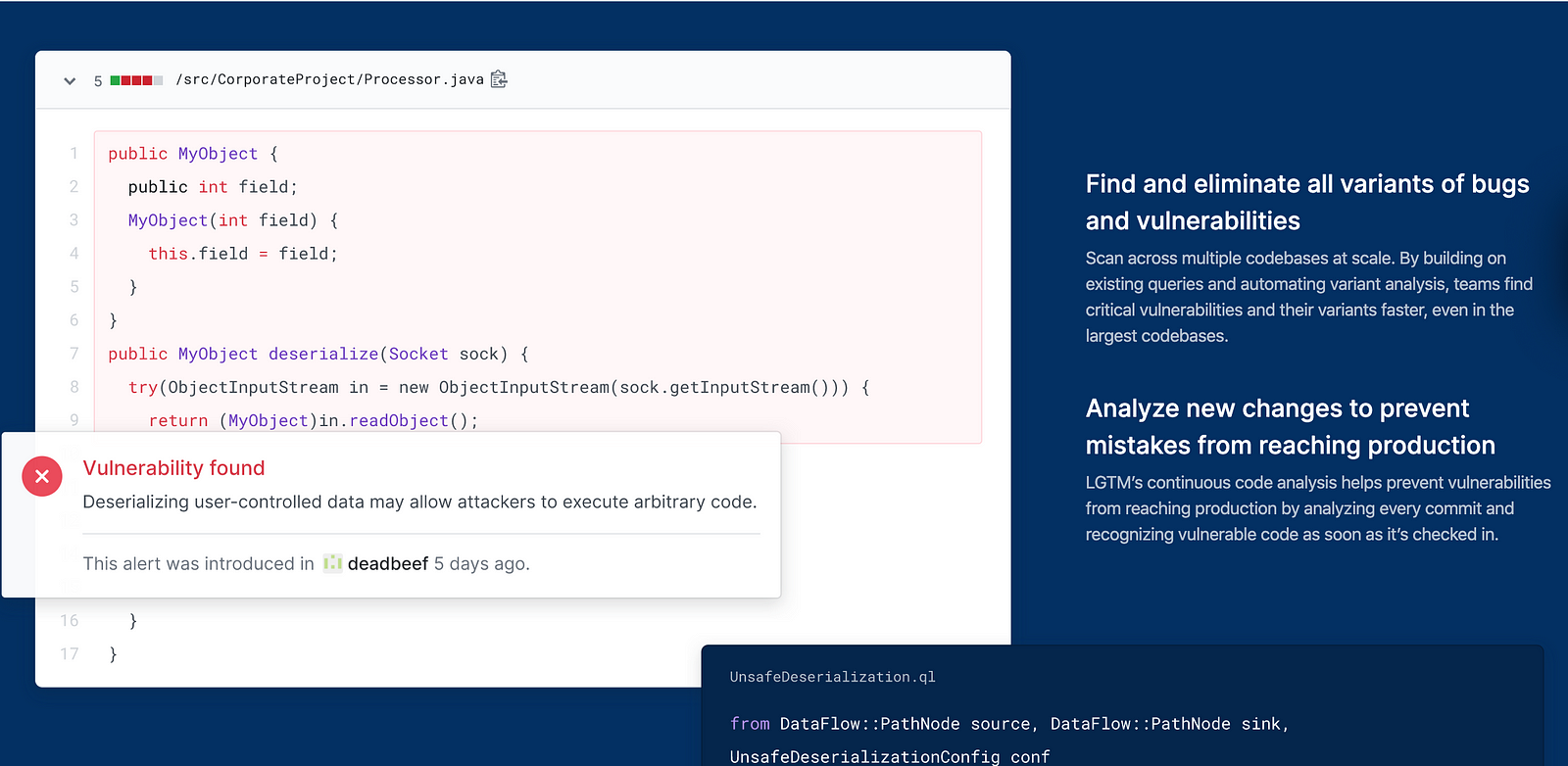
Check Vulnerability Databases
There’s a huge number of vulnerability databases that collate information on different types of vulnerabilities, and it is prudent to check them regularly. The CVE database is a good starting point because it contains a regularly updated list of publicly known cybersecurity vulnerabilities. Vuln is worth trying out as it has the latest database used by big organizations to monitor and identify open source vulnerabilities. OSS Index is also worth checking out; it is a database used by developers to identify open source dependencies and check for vulnerabilities.
